
When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.
Facebook's Abuse of Profiles & Root Certificates
In recent news, TechCrunch uncovered that Facebook was abusing Apple's Developer Enterprise Program, a platform that lets businesses distribute unreviewed apps to employees and sign certificates. Typically, this program is used to let workers test in-progress apps being developed before sending them up for App Store review, just like with the regular Developer Program, and it can be used to give workers mobile tools that the companies don't want available to outsiders. For an example of the latter, Google uses a Gbus app for employees only to request rides.
Facebook essentially suckered teenagers and adults into installing a data-collecting VPN app for "market research" purposes in exchange for $20 each month. Adults signed up right away while kids needed permission from their parents. They'd install a Facebook Research provisioning profile that included permissions to funnel TLS traffic through its VPN tunnel, as well as a root CA certificate that basically let them collect encrypted traffic coming to and from the iPhones for anything that was happening, not just Facebook related tasks. Any app's web use was recorded.
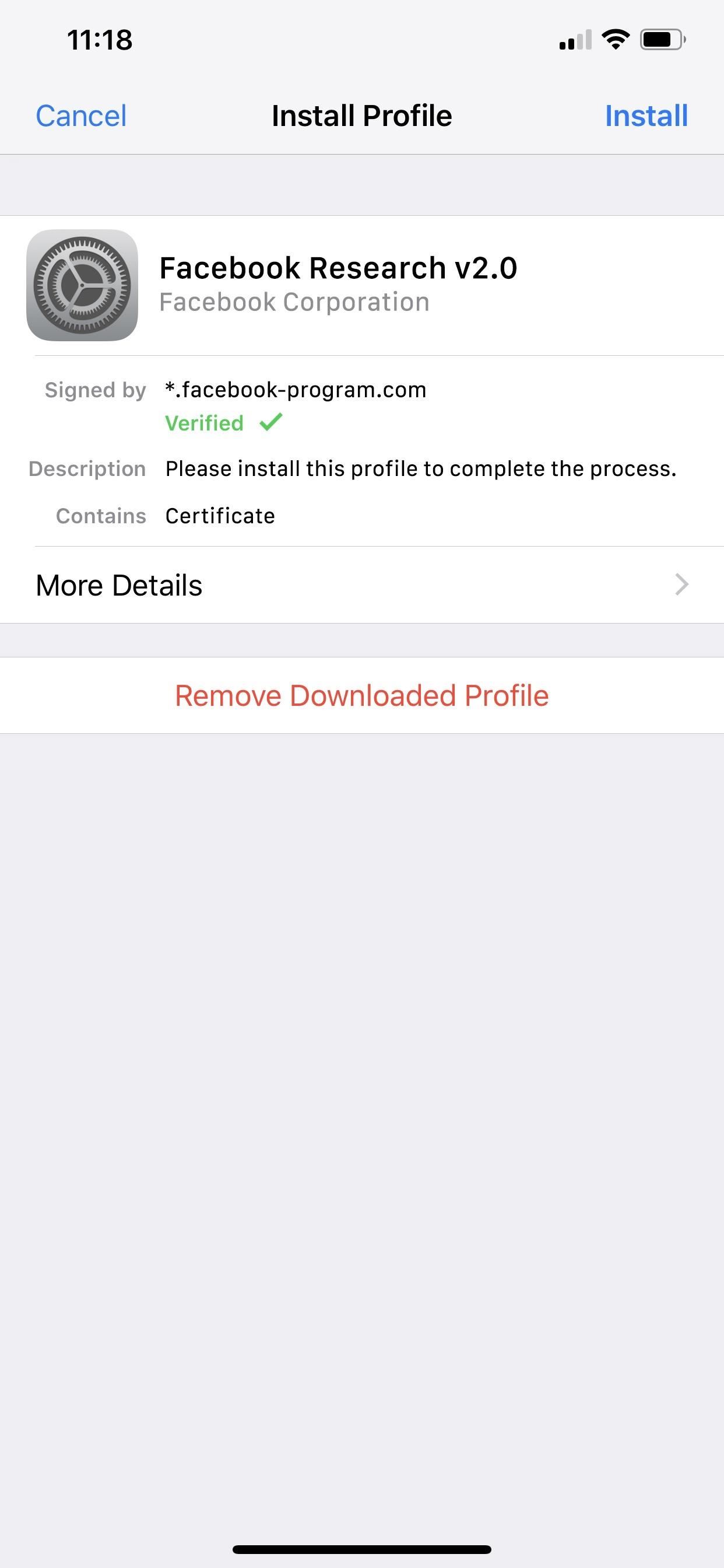
Although Apple is known for its stringent App Store guidelines that restrict vetted applications from harvesting data, the Developer Enterprise Program has virtually no oversight on any of the apps that are distributed using the certificate licenses it gives companies for $300 annually. And as for root certificates, Apple allows many on iOS 12, and it's blocked a few as well.
There Are Lots of Companies Abusing Certificates
Facebook isn't the only culprit abusing certificate licenses. For another big name example, Google was doing the exact same thing as Facebook, using a root CA certificate to grab any data going to and from the device for deep packet inspection. And while "trusted" root certificates are the biggest things to worry about, there are regular certificates as well as configuration profiles with or without them.
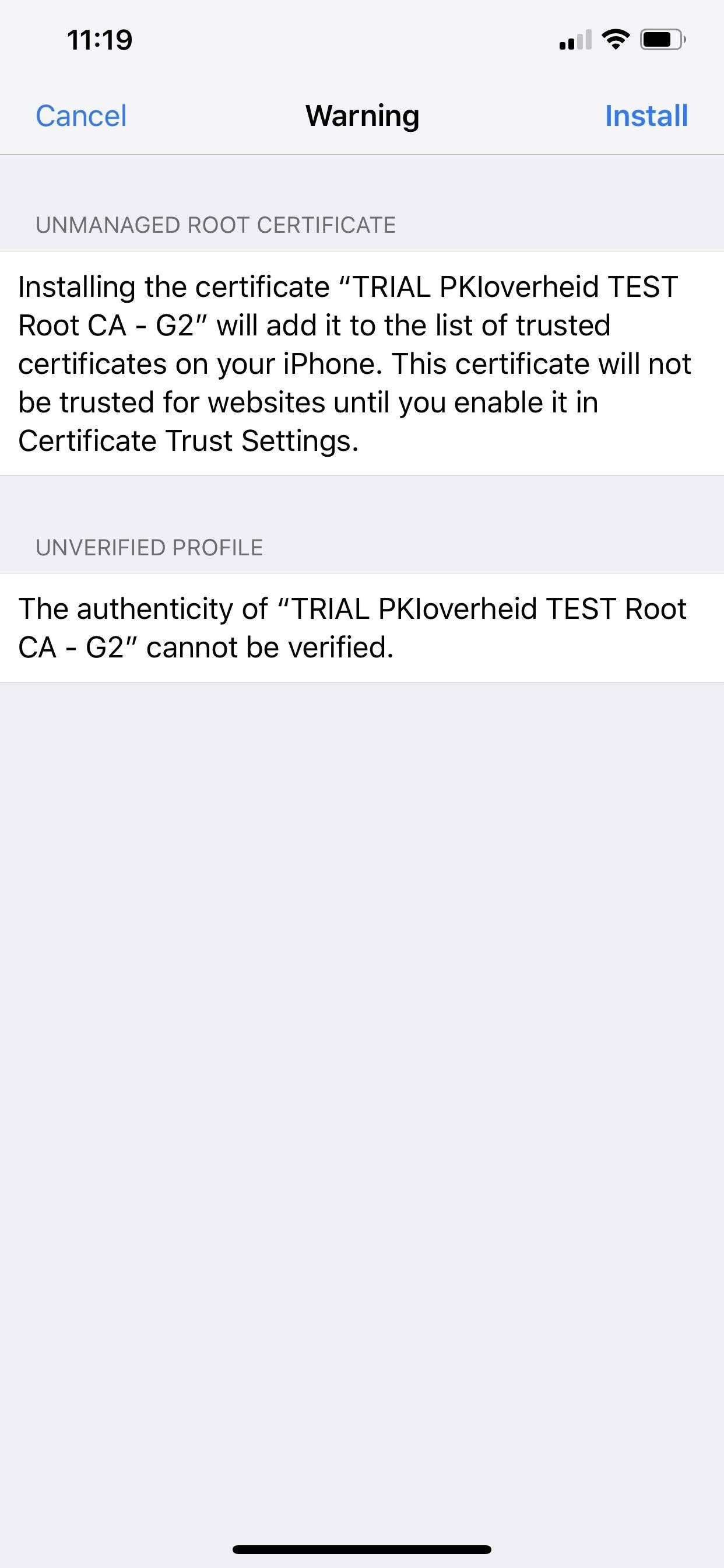
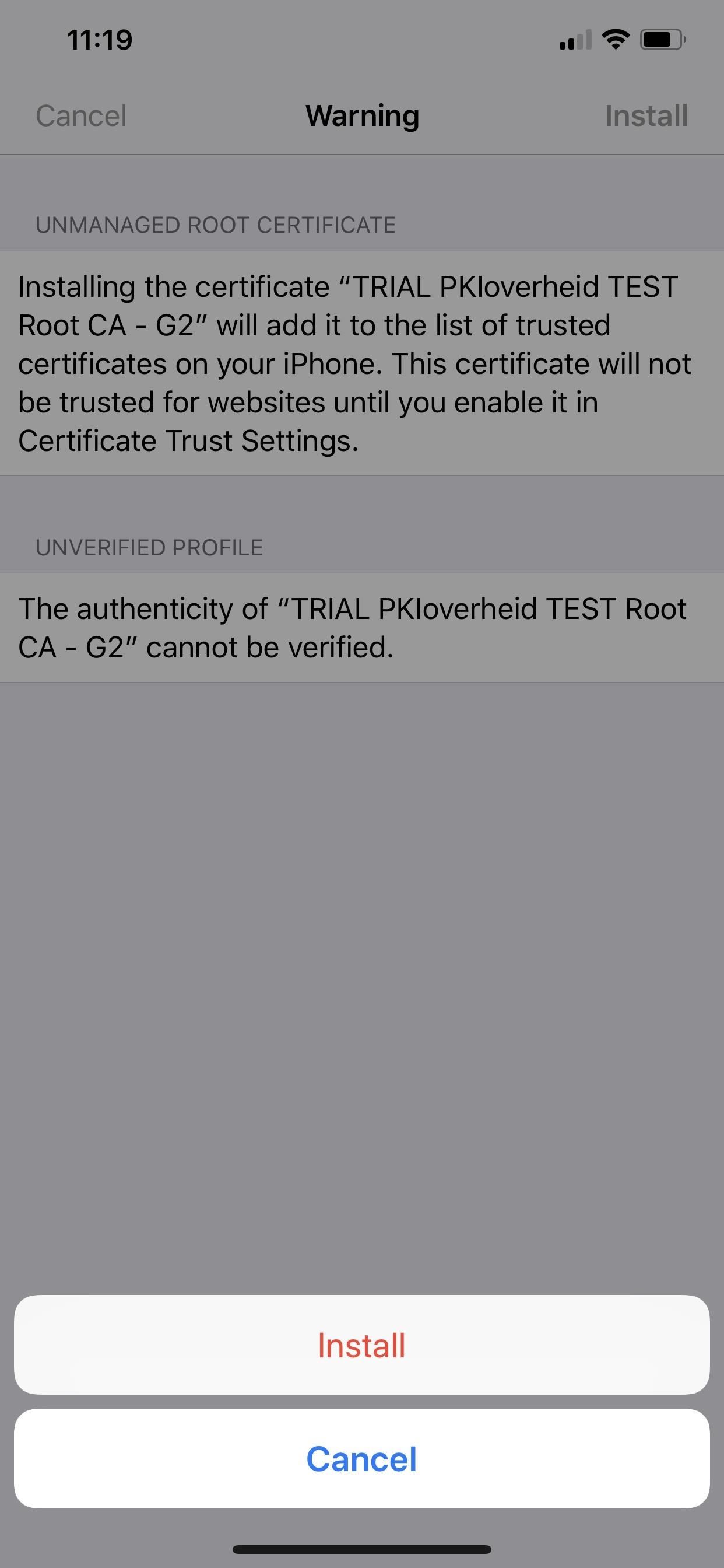
Anonymous program participants were using the Developer Enterprise Program to distribute porn and gambling apps, and shady developers took advantage to hand out cheating-based versions of popular apps such as Pokémon Go and Angry Birds, as well as pirated versions of paid apps like Spotify and Minecraft.
Unapproved app stores such as TutuApp, Panda Helper, AppValley, and TweakBox, as well as beta-testing platforms BetaBound, uTest, and Applause (which Facebook used), all require a profile installation, usually with a certificate (not necessarily a root one). The same goes for the apps they distribute, as well as solo apps found online. These profiles are easily installed just by tapping on a link in Safari.
Why Installing Certain Profiles & Certificates Is Bad
The data unapproved apps can siphon off your iPhone is near limitless with a root certificate, but that's not the only thing you have to worry about. Regular CA certificates and profiles can do just as much damage. When using apps that require a profile installation, even if you were unaware of what you were installing, they may ask you for payment details or passwords, something you shouldn't be so quick to give up.
Hackers and other malicious users could use social engineering to get you to install other configuration profiles, which house the certificates, that can include payloads for completing tasks such as creating new email accounts, serving you advertisements and pop-ups wherever you go, or exfiltrating data. And while VPN tunnels are of great concern, hacker's exploits could grab your personal data using a proxy server, changing APN settings, and using man-in-the-middle attacks.
For instance, there have been many related reports by users over the years where a website or email asked them to install a profile and certificate to get access to a weather widget, email app, or some other harmless-sounding feature, which in turn gave the profile permission to create new email accounts, redirect you to malicious websites, and serve ads.
Not All Profiles & Certificates Are Bad
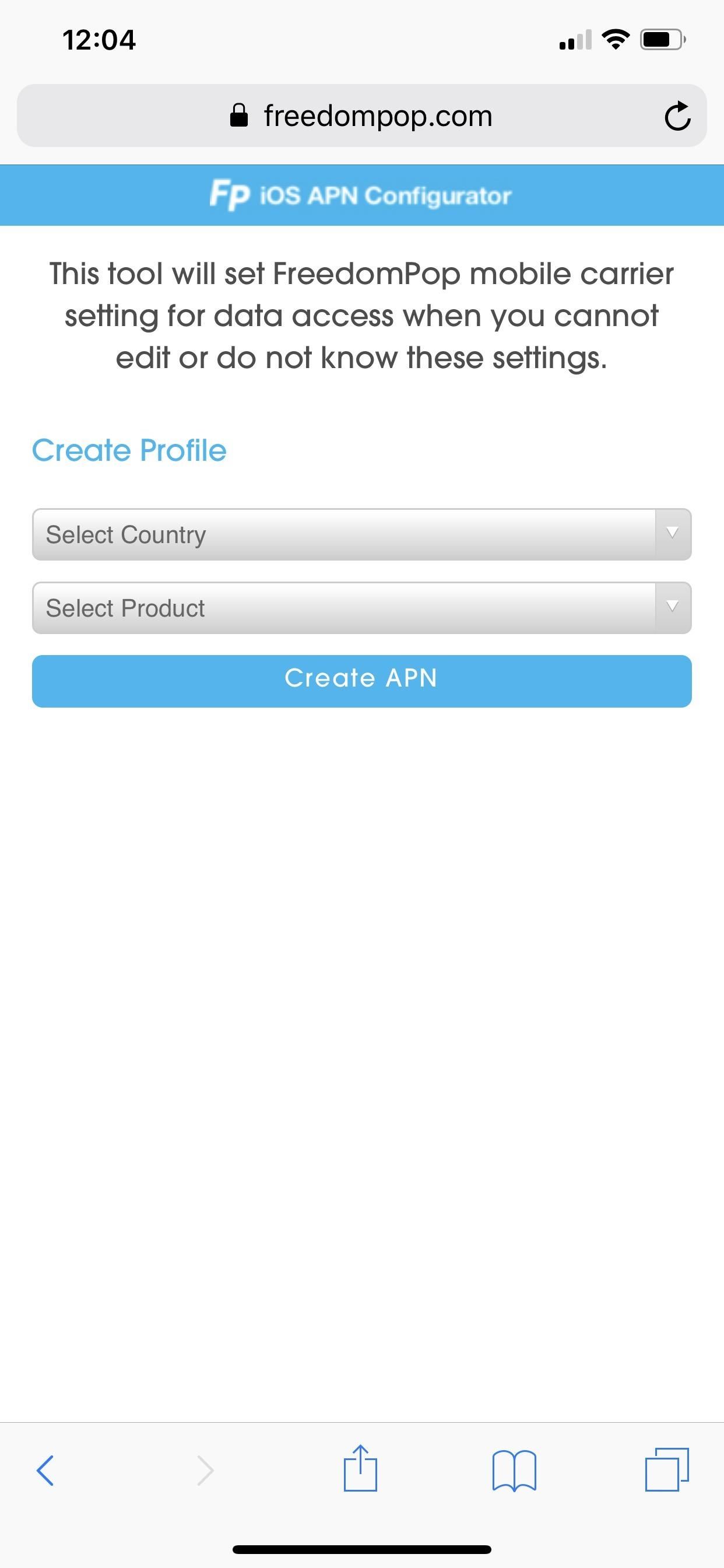
Apple uses its own program to distribute iOS beta software to developers and public beta testers, who then install a profile and certificate combo, and it's safe to say you can continue using those betas if you enjoy getting new features before everyone else. There are also services such as FreedomPop, which use these certificates to adjust APN cellular settings on your iPhone to provide free or low-cost data. Xfinity and LinkNYC use profiles to help users connect to public Wi-Fi hotspots.
Developers can also issue apps they're working on to a limited number of devices in their network before going through Apple's vigorous review process for App Store distribution. Companies, schools, and other places that hand out iPhones or iPads can employ Mobile Device Management profiles on supervised devices. Those profiles can do things such as block iOS updates, block other profiles from being installed, prevent certain apps from running, and even automatically trusting root CA certificates.
And then there are tools like Cydia Impactor which can be used to sideload IPA files for helpful apps such as Kodi, and they use your own Apple ID account information to give the apps permission to run. You could even use the Apple Configurator 2 utility to create a your own configuration profile to do things such as customize app icons on your iPhone without jailbreaking, which doesn't even require a signing certificate.
For information on how certificates work across Apple's platform, check out Apple's description of digital certificates in its cryptography reference.
How to Check Your iPhone Root Certificates
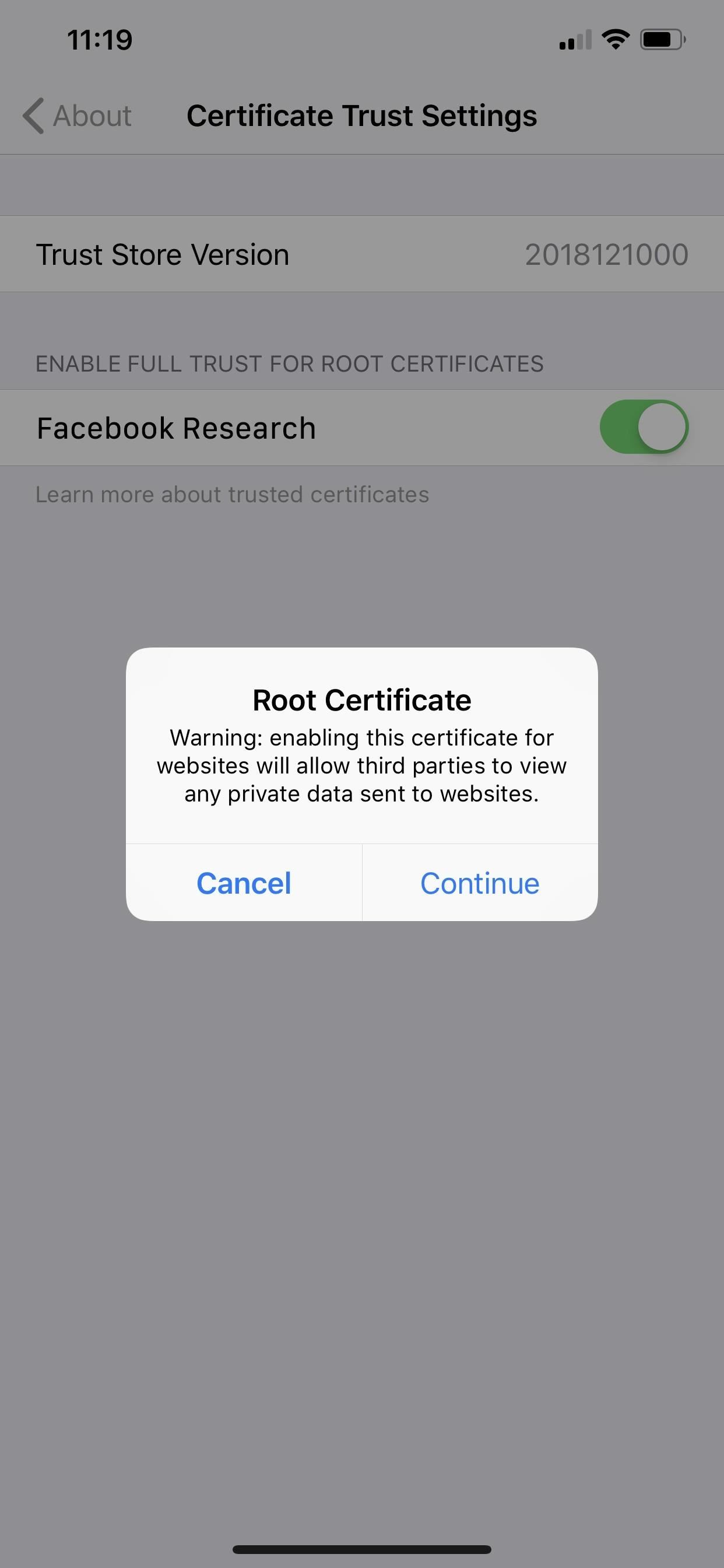
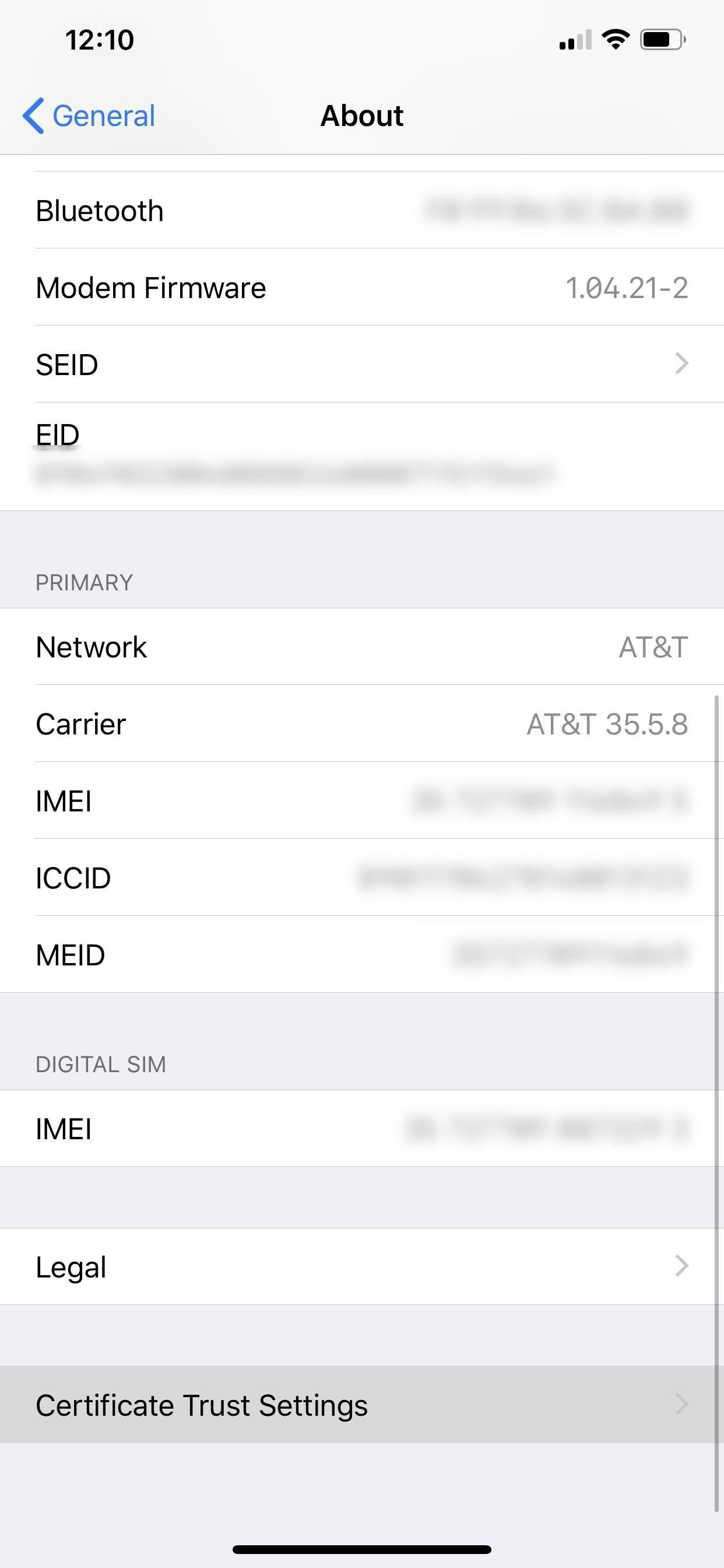
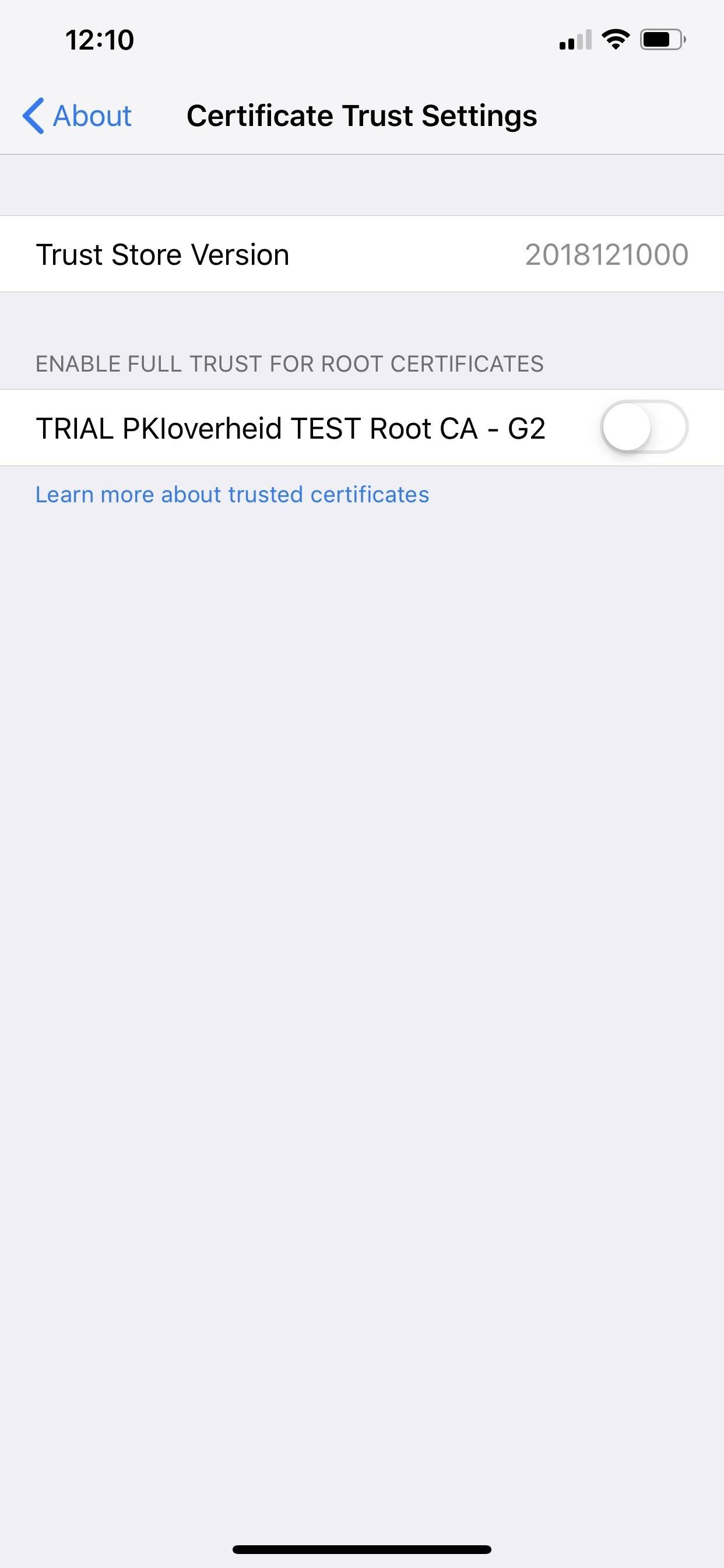
Don't know if you've downloaded a profile with a root or regular certificate on your device? Luckily, it's easy to not only check but also to remove them from your iPhone. First, to check if you have any trusted root CA certificates, go to Settings –> General –> About –> Certificate Trust Settings.
If there are any here, they'll appear under the "Trust Store Version." If they're green, they're running right now. Root certificates here that were deployed via Apple Configurator or Mobile Device Management are automatically trusted. You can toggle it off to disable it, but that won't delete it, so you'll want to view the next section for that.
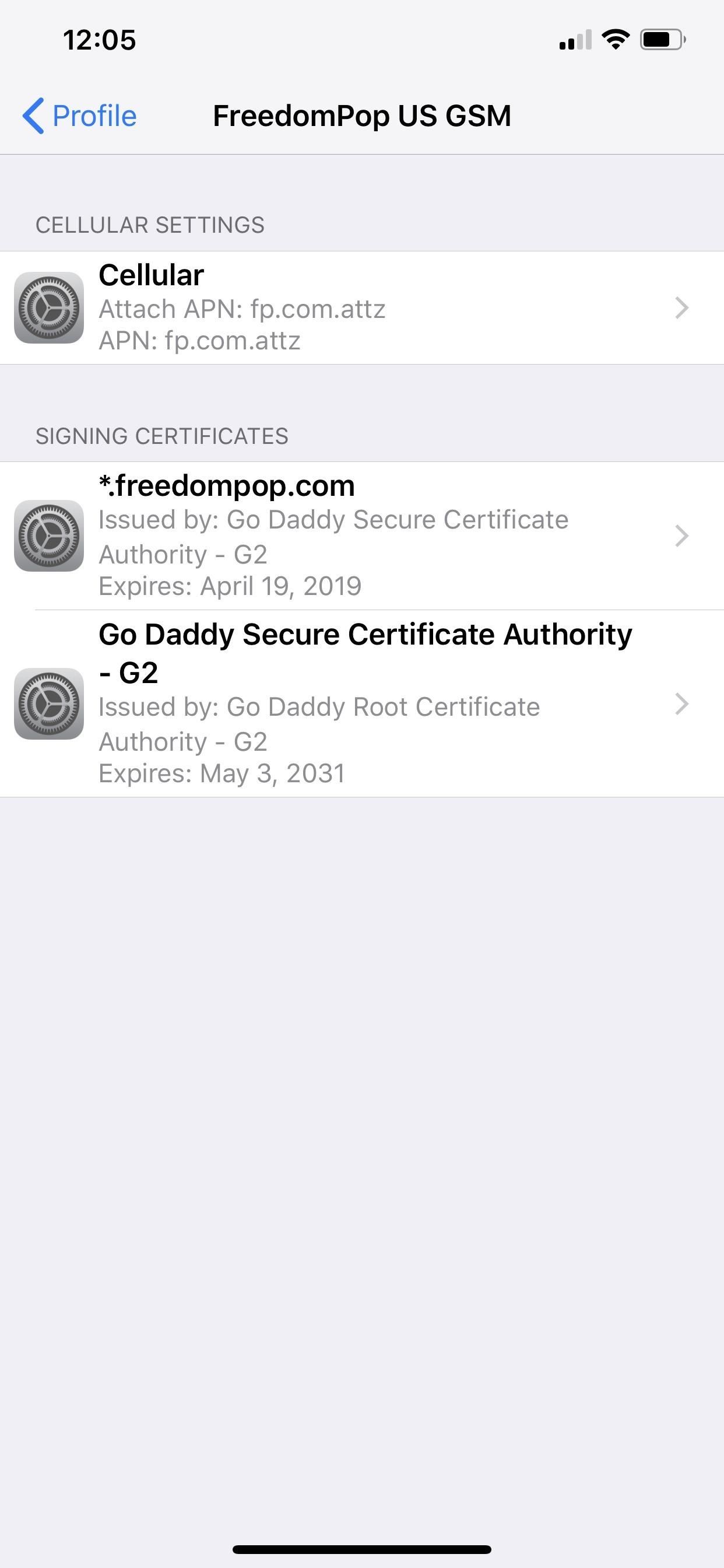
How to Check Your iPhone Profiles & Other Certificates
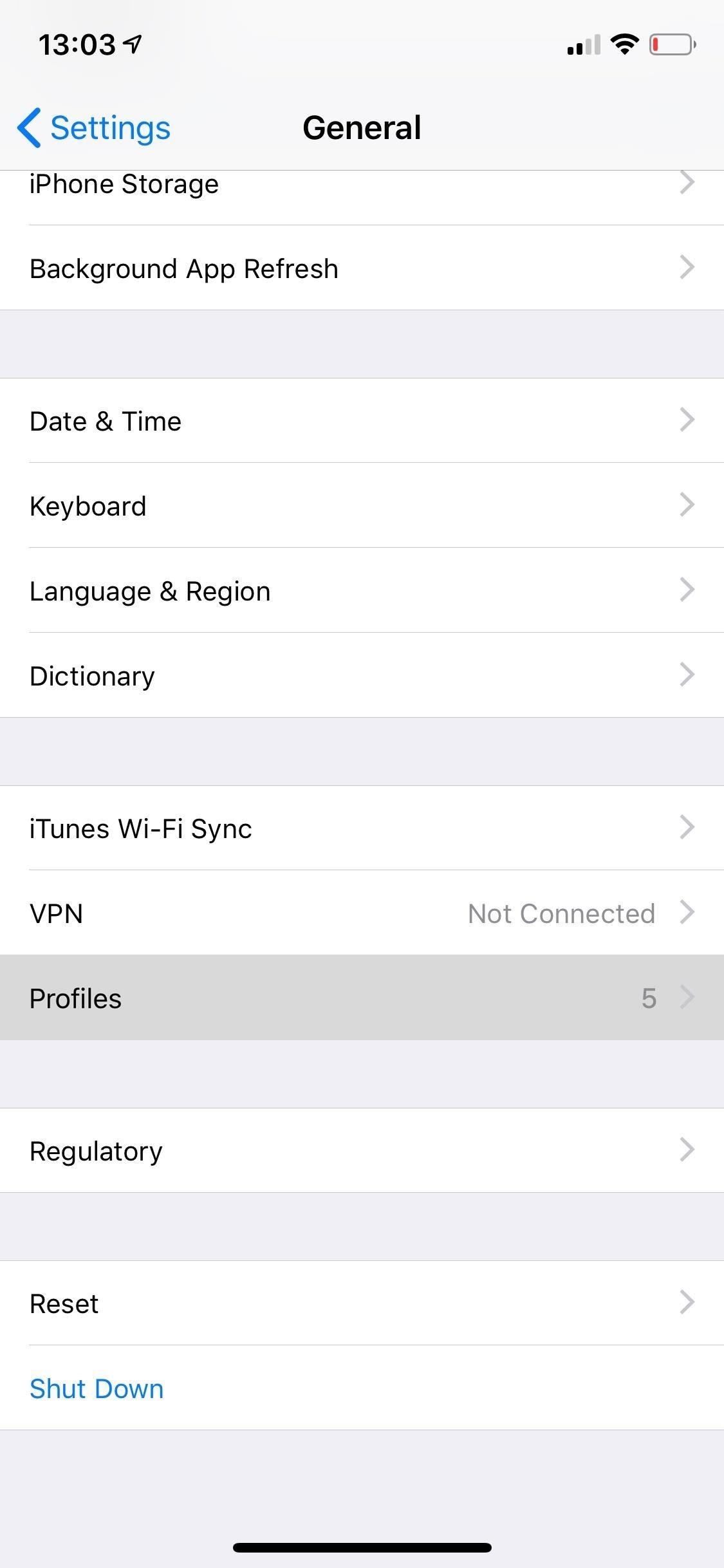
To view any existing profiles and/or certificates on your device, go to the Settings application, tap on "General," and scroll down to "Profile/s." If there is not "Profile/s" section, you have none installed. If you do see it, tap on it to view them.
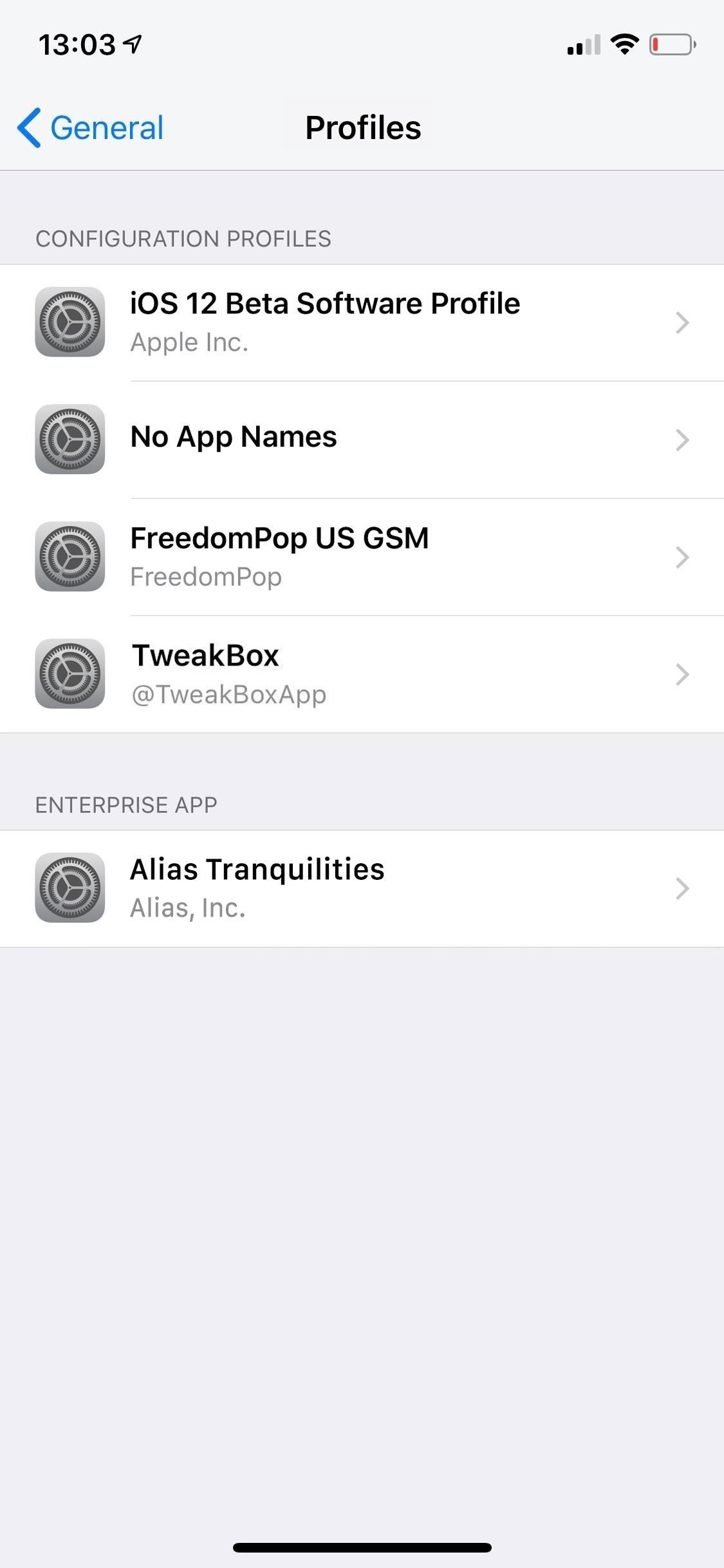
On this page, there can be three different types of profiles, each which can include provisions for settings on your device as well as certificates. They are configuration profiles, mobile device management, and enterprise apps.
How to Remove Unwanted Profiles & Certificates for Good
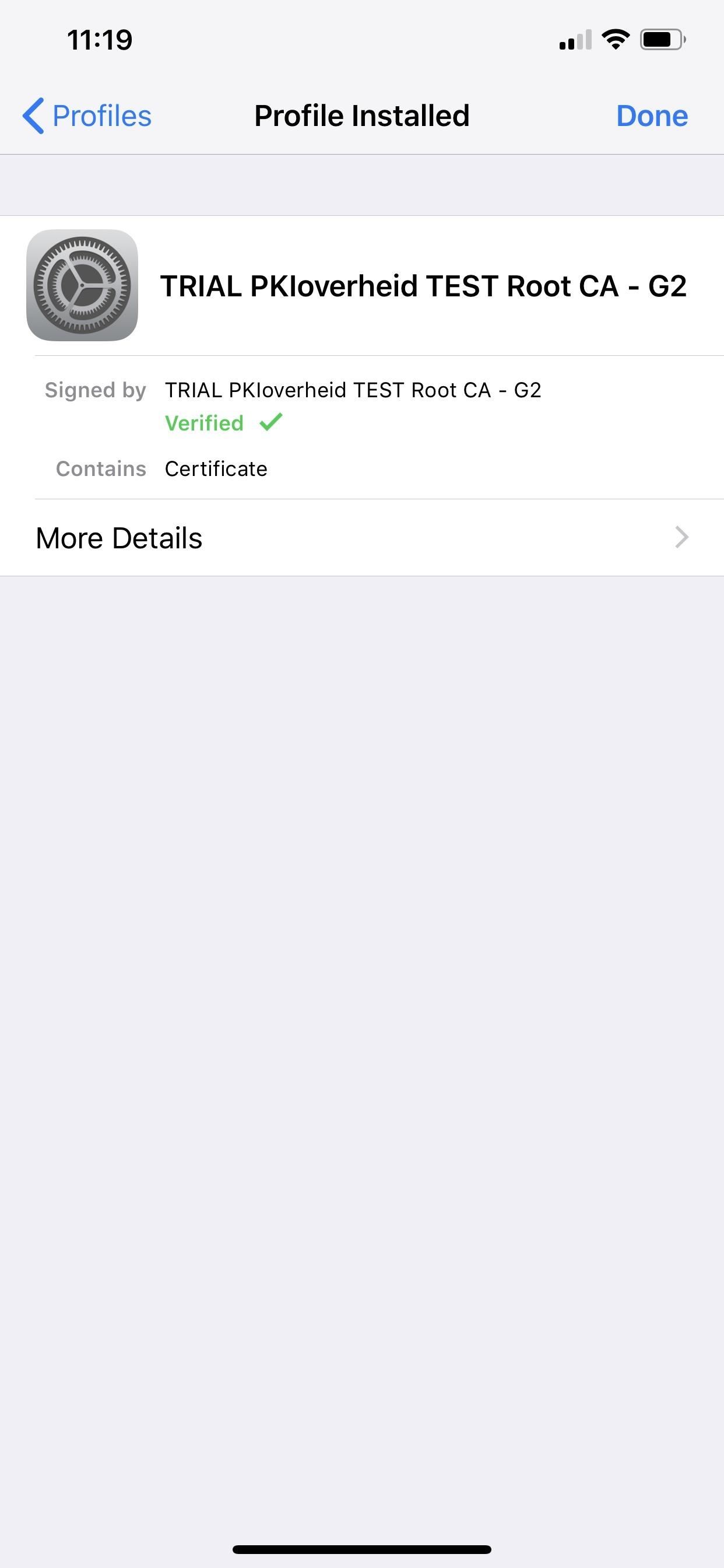
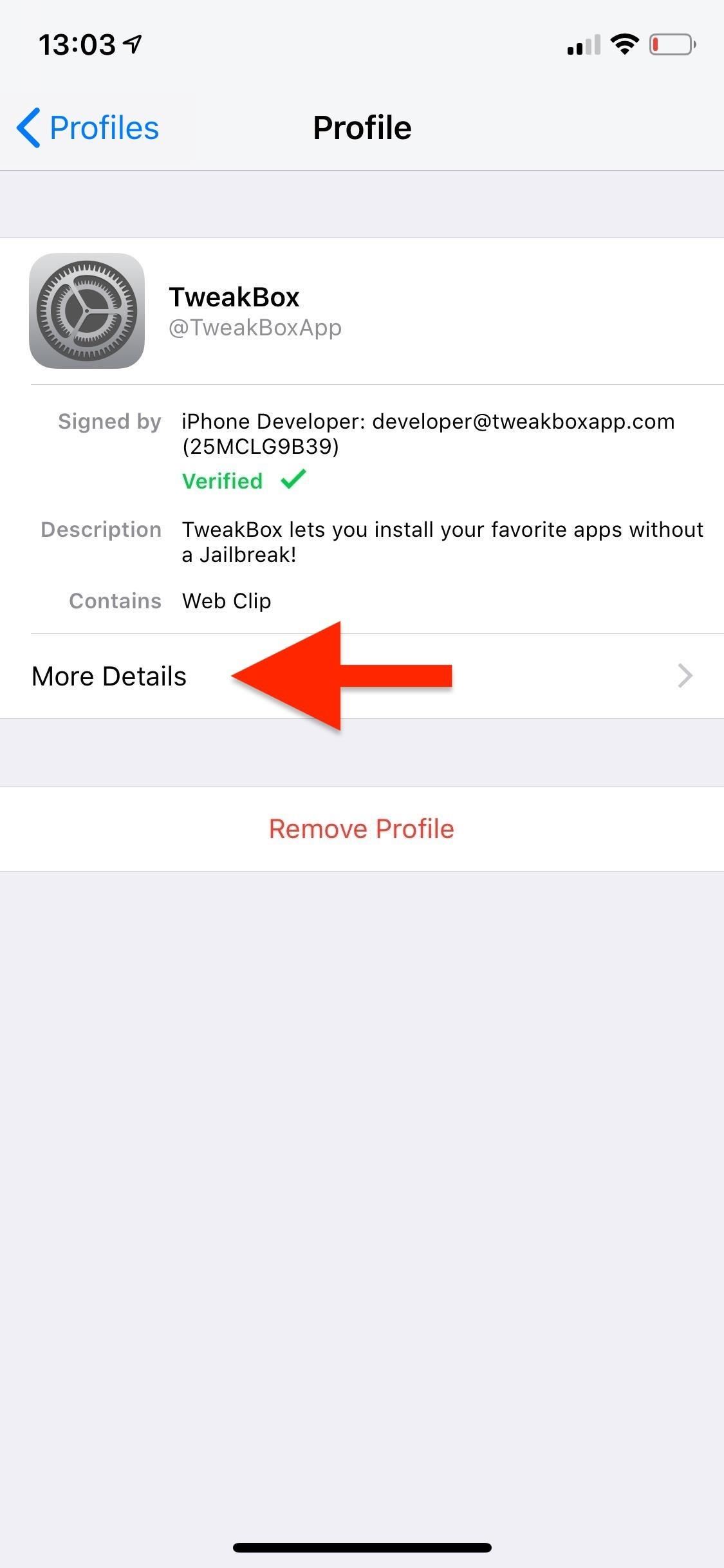
Inside the profile, you can see who it's signed by and a short description of it. In some cases, it may not be signed at all, such as when you use Apple Configurator 2 to build a custom profile for yourself.
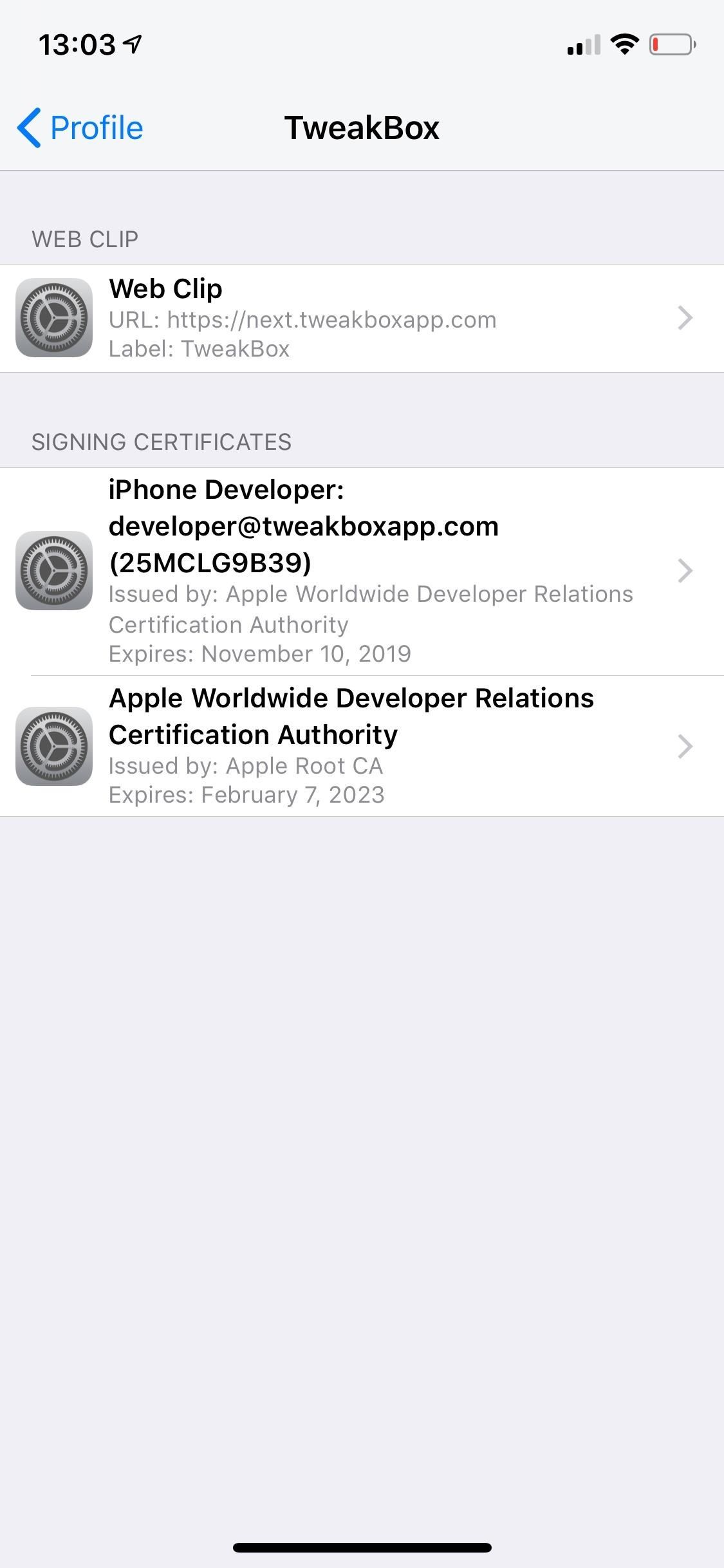
If you tap on "More Details," you can see what's inside the configuration profile, which usually includes a "signing" certificate and sometimes permissions to adjust things such as internal settings, cellular configurations, VPN information, etc. You can tap on the certificates to view more information about them.
In my example for the TweakBox profile, there's a regular CA certificate titled "Apple Worldwide Developer Relations Certification Authority." This is not a root certificate, but it's still something I don't need.
To delete the profile and certificates, go back to the profile view and tap on "Remove Profile." Enter your passcode when prompted, tap on "Remove," and the root certificate will be removed from your device. Doing this will also remove all permissions given in the first place, should wipe all settings changes by the profile, and will remove or force connected apps from working.
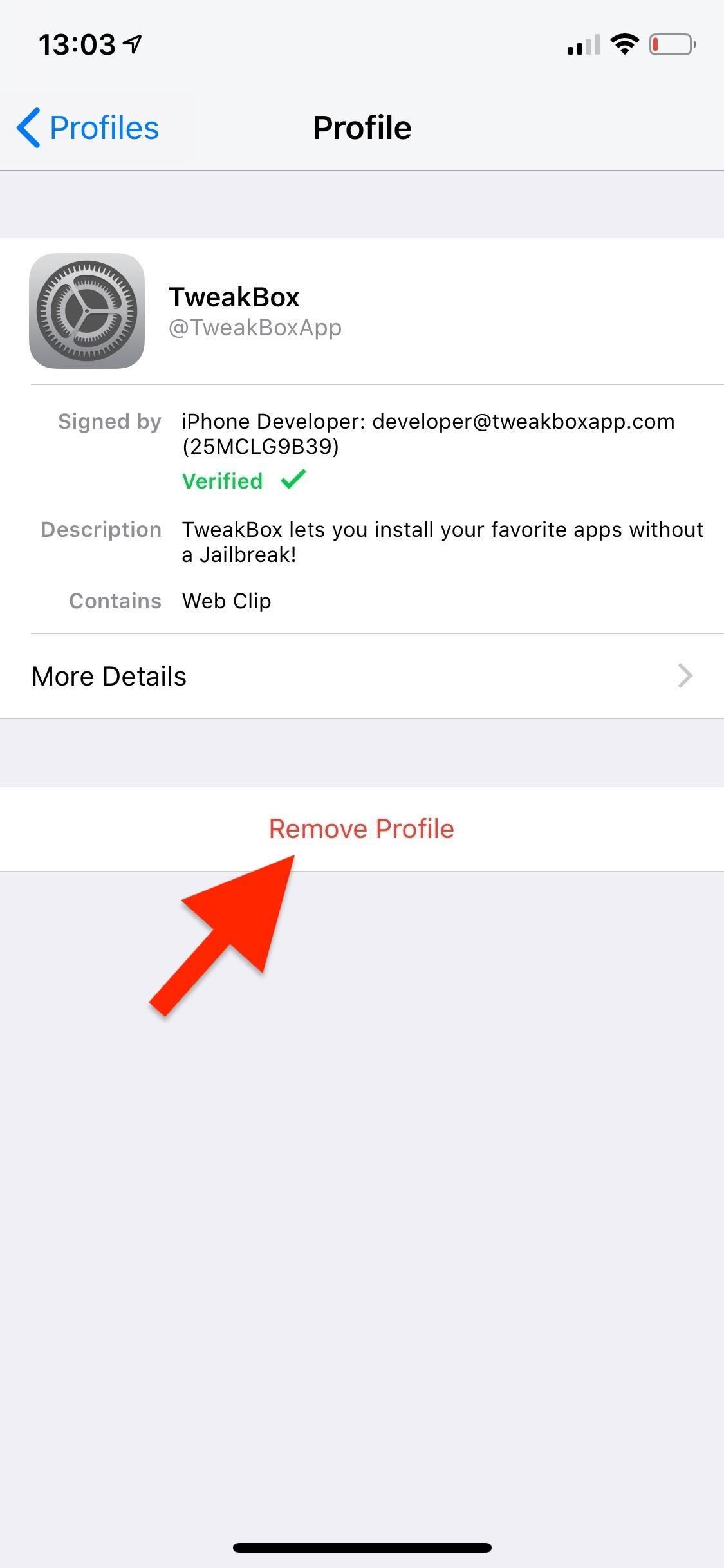
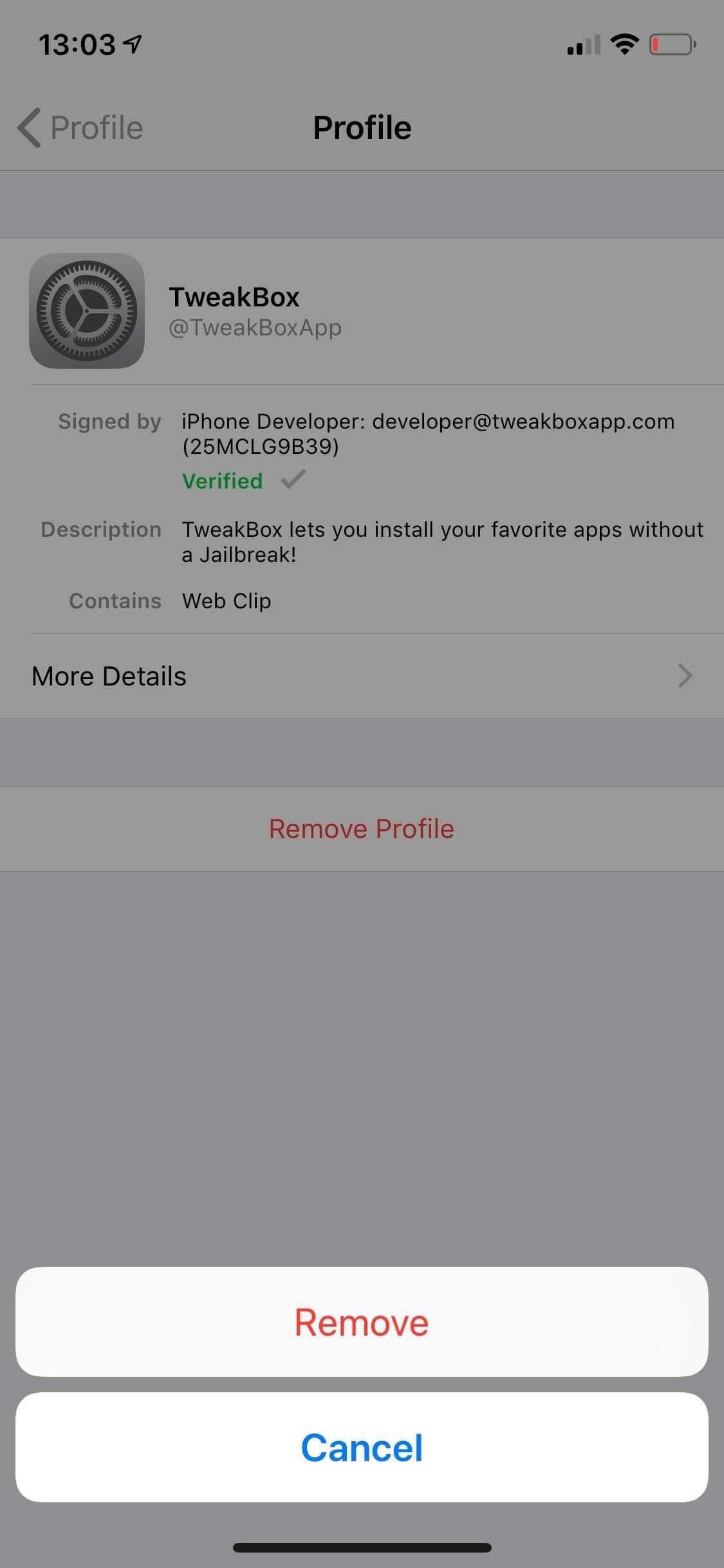
For enterprise apps, select the profile, then tap "Delete App," followed by "Delete App" on the pop-up. This will remove the app and enterprise profile. You can also delete an enterprise app on your home screen like any other app, and it will also remove its profile unless the profile has more than one enterprise app attached to it.
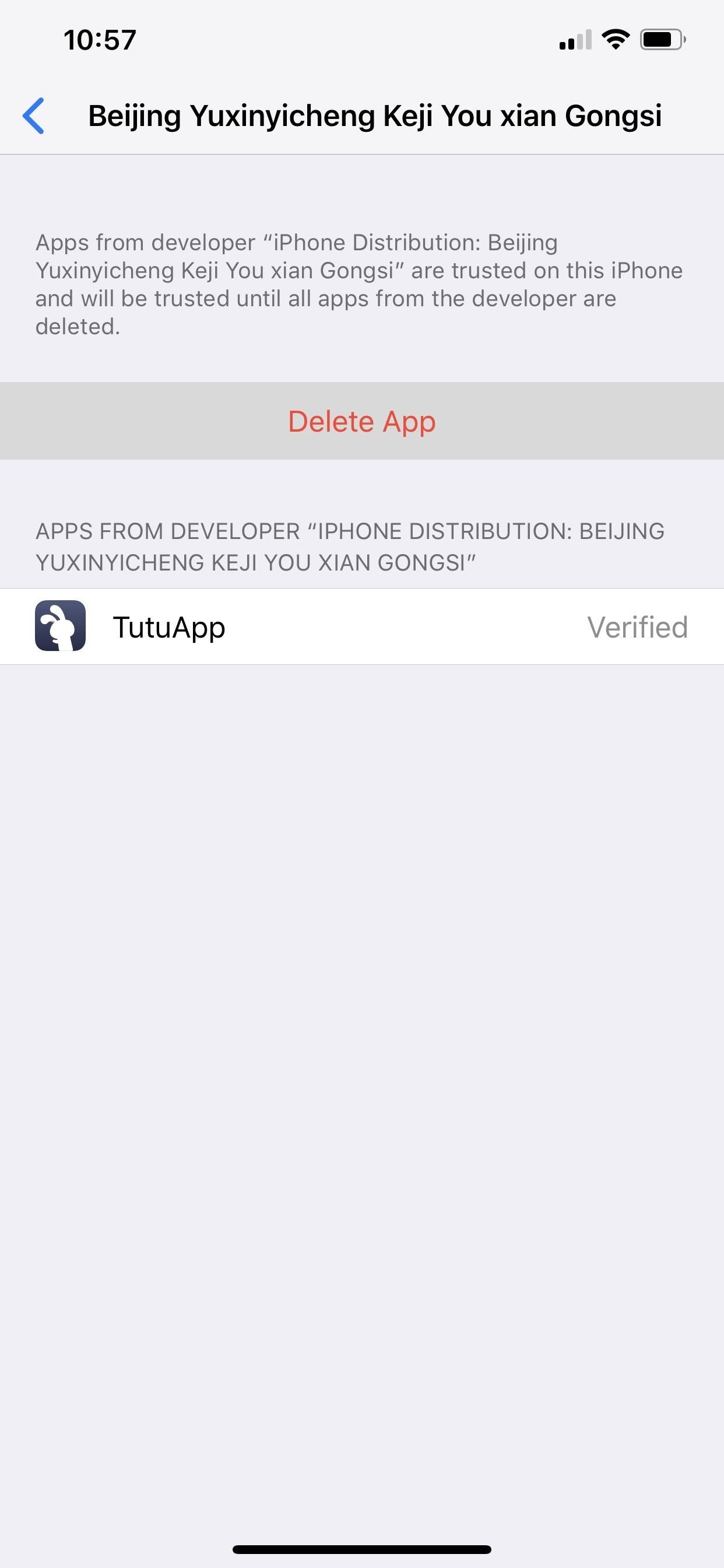
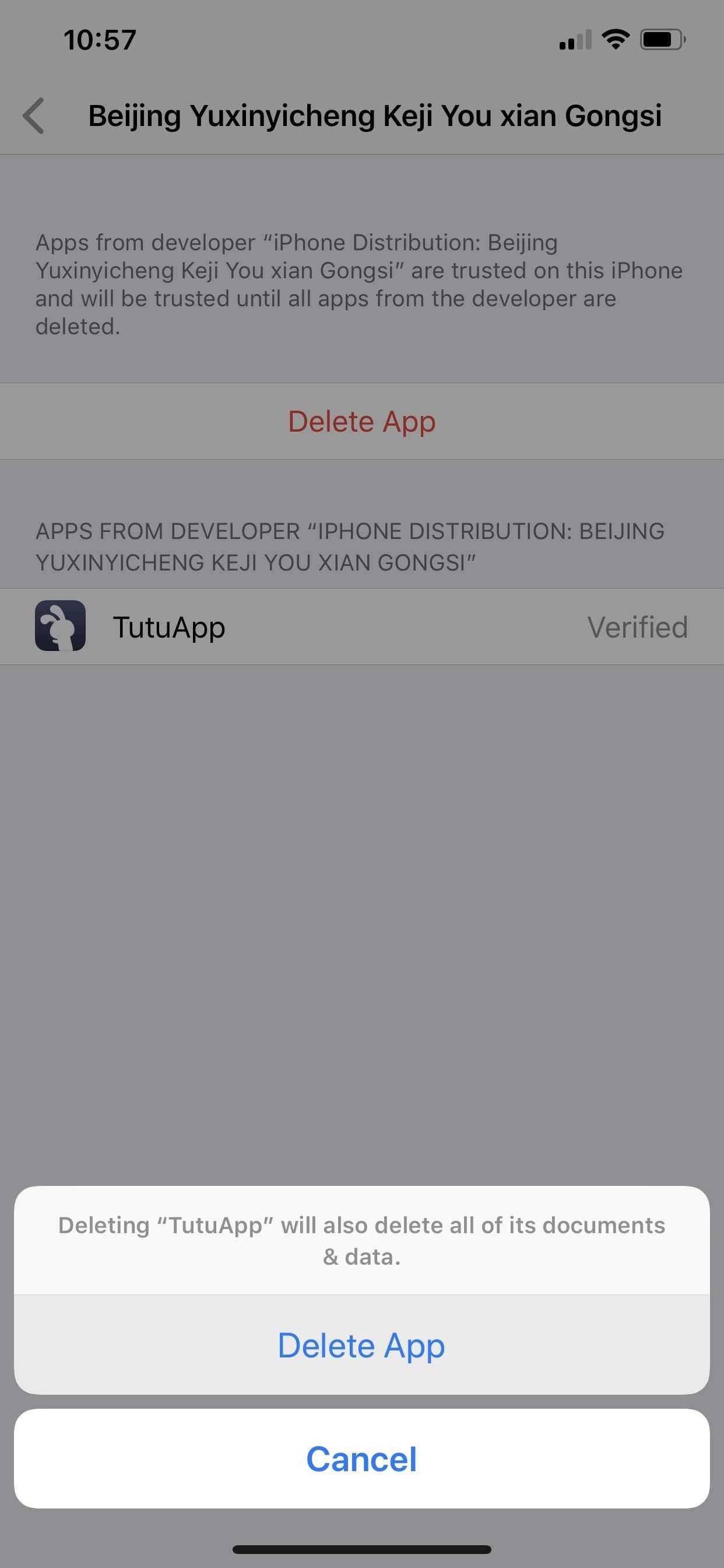
With the profile and/or certificates deleted, your private information, such as web activity and secure transactions, can no longer be accessed by the organization you got it from or tricked you into installing it.
This article was produced during Gadget Hacks' special coverage on smartphone privacy and security. Check out the whole Privacy and Security series.
Just updated your iPhone? You'll find new features for Podcasts, News, Books, and TV, as well as important security improvements and fresh wallpapers. Find out what's new and changed on your iPhone with the iOS 17.5 update.




















9 Comments
Need help. Been dealing with an issue of remote device management/domination since late February and I've gone through 5 phones and 5 phone # changes and about 9 appleid accounts. I even moved to a new city. Imei, serial numbers, iccid, have changed, of course, with each new phone. Only constant in all this is my carrier, myself, and the TRUSTED STORE VERSION: 2018121000. I've been cut of from parts of the internet, harassed, mocked, dealt with phone playing/making noise when I'm trying to sleep and so on. The hardest part was trying to figure out the issue when your denied access to information. But I believe that this is the "bug" how they have installed it idk, new phone again. This is the 5th one and I've only had it 2 1/2 days. I've tried everything I could. Factory resets, updates, antivirus, vpn, starting over with new everything. On this phone I hadn't even created an appleid for this phone yet when is was compromised. I was going out of town later that evening and figured I'd set up the phone when I got there, but it was too late. It was taken already. It also doesn't give me an option to to turn on or off and they are masking it in profiles. Finally found info today that this cert is used for MDM. Please. Any info will be greatly appreciated.
E V E R Y T G I N G you have described i am going thru to the T. Its been a year , i moved from ohio to seattle , spent thousands of dollars on new devices and the sane amount of hours trying to figure this out . Have you got any clues since u last posted ? Everyone thinks im insane
Me too! Listen guys can you contact me on my artist page? I have an idea. Comment something on my artist page "gracelesslacy" on FB and I will explain. I have some videos there too that might be helpful.
Oh yeah I basically got forced out of my home and was homeless for a year because it got so bad. I've been dealing with this for at least 3 years now and I have some clues that might help. I have countless posts on socitoo.. media about it too... I even made a few discrete videos here and there. It has ruined my business, my social life, and alienated me from family and people I thought were my friends... My situation is really bizarre. I am curious about a few factors that maybe if we can compare our situations so we can come up with some answers based on deductive reasoning too. I am compiling a crapload of data and I'm getting ready to get my websites back up and I think I'm going to host them myself but I'm trying to get certified in the fundamentals of arduino because I know that's part of the issue I'm dealing with. Someone created a far reaching a mesh network using BLEand other IOT devices programming them to act as nodes in a client-server relationship which allows them to mitigate cyber security protections via standard routers and the ones with Beamforming or 5G are a whole bother story. Someone also altered my FB app so I would get a broken link with"Portal" which I never even heard of until ads started showing up on my FB like a month ago and when I tried to log in from a browser I got a broken link with all of this Apple open source bs... so yeah hit me up and I'll explain more. 3 years you guys....
Hi am going through the same situation Iit would be much appreciated if you could give me Information about how to delete these trust store versions and trust assets versions it feels as if someone is blocking al my access to websites through my Wi-Fi so I had to turn it off an use mobile data to gain access to this site please help thanks in advance
Hello, I'm having similar issues that have been going on since 2018. I also have changed everything many times but still being restricted. Could you please contact me!
Jmaddox76@protonmail.com
According to apple customer service and their website it should be this
And I know it's not that there is no profile there.. sometime is says profile but shows no profile when I click on the profile tab and as this picture shows, sometimes it doesn't show the profile tab at. I know I'm cut of from portions of my settings and hindered on my web searches by what turns up when I researching this issue. For instance I ask how to disable an app or opt out of something on IPhone Xr and I only get results of how to enroll or enable but not just iPhone it shows android, laptops, everything else that I'm not asking basically. But when profiles is on there that's when it becomes really "interactive" as if someone is presently blocking my moves or closing pages, apps, or settings on me.
I know EXACTLY what you are going through. I have been studying this same type of thing for the past 3 years and I have been lucky enough to be able to find a lot of the answers I have been looking for, but it's very unfortunate that these things are not common knowledge and I still need more answers . I don't want to say too much but I'm compiling a timeline with a buttload of evidence to have on standby should something go south in the event that I get blamed for something I'm not responsible for. I would be interested to compare notes . ... and if it's any consolation I don't think you are crazy, at all. It is very possible for someone to "hide" a "profile" as well. I have a page on FB called "Internet of Things Security" and I thought about posting some info there but if you want to contact me just comment on one of my posts on my artist page on FB "Gracelesslacy" and I may be able to answer some of the questions you have about your situation because like I said I have been going through it for like 3 years now and I have some ideas on how to deal with it, but you are the first person I've seen who has been dealing with the same thing.
Share Your Thoughts