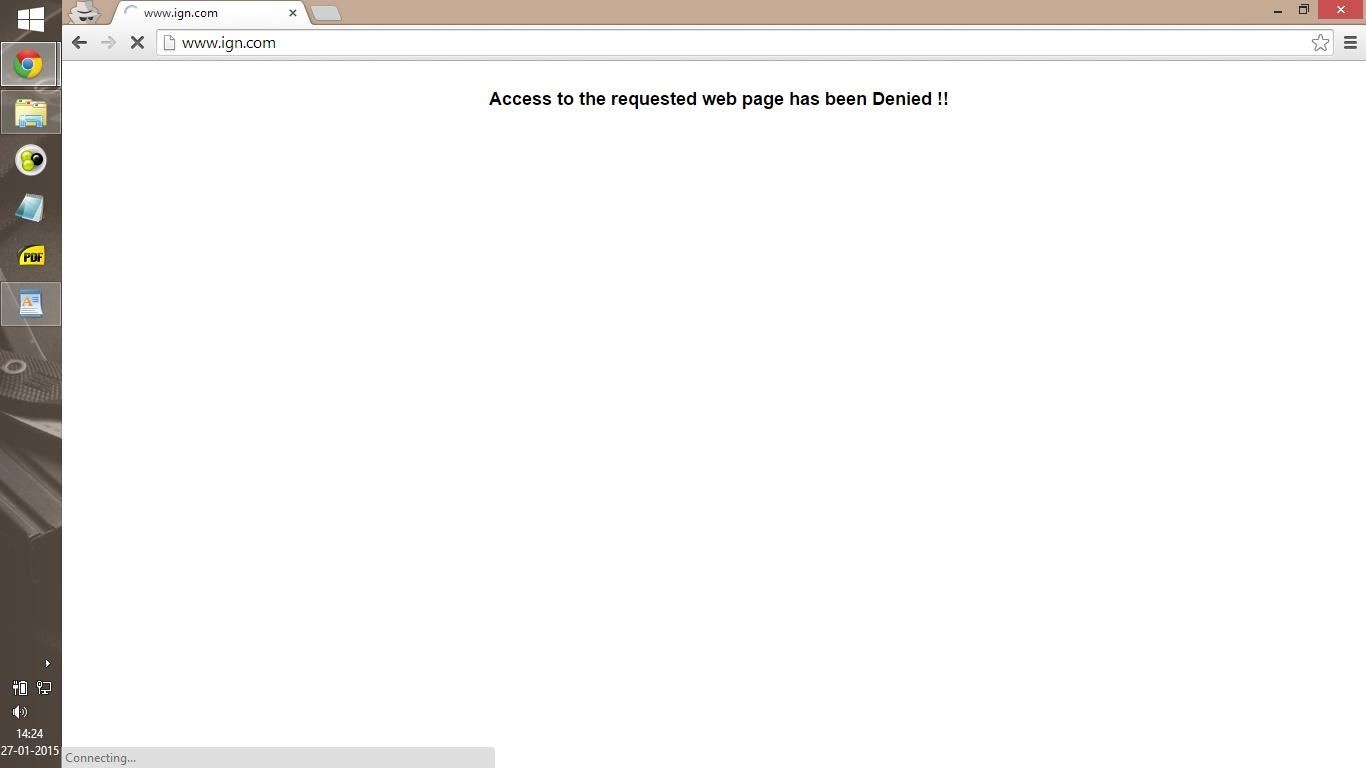
I work in a institute where accesss to some websites has been blocked and any attempt to open them in browser results in a custom message.
But a TCP Traceroute using hping3 or Nmap shows that the request is reaching the website server.
(IP address verified using nslookup on the same network, even nslookup working)
So what exactly is happening here?
Can anyone explain ?
Edit : I am attaching the traceroute output along with the browser output.
root@kali:~# ifconfig eth0
eth0 Link encap:Ethernet HWaddr 84:34:97:6f:ac:40
inet addr:172.17.18.166 Bcast:172.17.18.255 Mask:255.255.255.0
inet6 addr: fe80::8865:97ff:fe6f:ac40/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5014 errors:0 dropped:0 overruns:0 frame:0
TX packets:55 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:389682 (380.5 KiB) TX bytes:4683 (4.5 KiB)
root@kali:~# nslookup ign.com
Server: 172.24.2.71
Address: 172.24.2.71#53
Non-authoritative answer:
Name: ign.com
Address: 54.208.208.217
root@kali:~# traceroute ign.com
traceroute to ign.com (54.208.208.217), 30 hops max, 60 byte packets
1 172.17.18.254 (172.17.18.254) 3.844 ms 3.891 ms 4.185 ms
2 172.24.0.254 (172.24.0.254) 2.538 ms 2.613 ms 2.660 ms
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
root@kali:~# hping3 -z -t 1 -S ign.com -p 80
HPING ign.com (eth0 54.209.144.209): S set, 40 headers + 0 data bytes
TTL 0 during transit from ip=172.17.18.254 name=UNKNOWN
TTL 0 during transit from ip=172.17.18.254 name=UNKNOWN
2: TTL 0 during transit from ip=172.24.0.254 name=UNKNOWN
TTL 0 during transit from ip=172.24.0.254 name=UNKNOWN
TTL 0 during transit from ip=172.24.0.254 name=UNKNOWN
3: len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=22 win=5840 rtt=0.6 ms
len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=23 win=5840 rtt=0.6 ms
len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=24 win=5840 rtt=0.5 ms
len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=25 win=5840 rtt=0.5 ms
4: len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=26 win=5840 rtt=0.4 ms
len=46 ip=54.209.144.209 ttl=62 DF id=0 sport=80 flags=SA seq=27 win=5840 rtt=0.8 ms
^C
--- ign.com hping statistic ---
28 packets transmitted, 11 packets received, 61% packet loss
round-trip min/avg/max = 0.4/0.6/0.8 ms
root@kali:~# nmap --traceroute ign.com
Starting Nmap 6.47 ( http://nmap.org ) at 2015-01-27 14:16 UTC
Nmap scan report for ign.com (54.209.144.209)
Host is up (0.00043s latency).
rDNS record for 54.209.144.209: ec2-54-209-144-209.compute-1.amazonaws.com
Not shown: 997 filtered ports
PORT STATE SERVICE
21/tcp open ftp
80/tcp open http
443/tcp open https
TRACEROUTE (using port 443/tcp)
HOP RTT ADDRESS
1 0.77 ms 172.17.18.254
2 0.42 ms 172.24.0.254
3 ...
4 0.48 ms ec2-54-209-144-209.compute-1.amazonaws.com (54.209.144.209)
Nmap done: 1 IP address (1 host up) scanned in 23.02 seconds








































6 Responses
Mike:
You provide very little info about the content filtering at your institute, but I can speculate on how some content filtering works.
First, there is usually a proxy between you and the Internet. That proxy provides the filtering. Although it may allow TCP packets out, it may filter on only HTTP and HTTPS. That's why the TCP traceroute would work, but not the HTTP request.
OTW
Hey,
If I would be in your situation I would probably enable port forwarding on my router at home in order to forward a random port to a http proxy of my choice.
You can use lists like the following which will provide you the required proxy.
https://www.new-proxies.com/
Let me know if my idea is rubbish ;)
Good luck,
Rob
More information is required for us to help you. All of your threads are very vague giving us very little to work with.
ghost_
Sorry sir, I will be more descriptive in my future posts.
As of now, I am attaching the results of a normal traceroute, hping traceroute and nmap traceroute to a blocked website.
Please checkout the edits in the original post in a couple of mins.
Hope it helps...
simply use a proxy with tunneling. Try googling "free proxies".
Or use Tor (which is basically a proxies network)
Be sure that these techniques are forbidden by your compagny policies and you may have trouble for trying to escape the institute's proxy.
Mike they might have changed the hosts file so that some websites will redirect you to blank pages. Also you can get around this with tor or a vpn.
Share Your Thoughts